Traditional antivirus solutions struggle against today’s increasingly sophisticated cyber threats. Endpoint detection & response (EDR) technology offers a next-generation approach, leveraging AI and continuous monitoring to protect companies against security risks. EDR provides:
- Proactive Detection: EDR goes beyond signature-based protection, identifying suspicious activities indicative of novel threats.
- Deep Insights: It analyzes both file content and program behavior, painting a comprehensive picture of endpoint activity.
- Rapid Response: Upon threat detection, EDR can automatically isolate devices, block processes, or quarantine files, minimizing damage.
- Managed Services: EDR solutions like Omega’s provide expert monitoring and response, easing the burden on internal security teams.


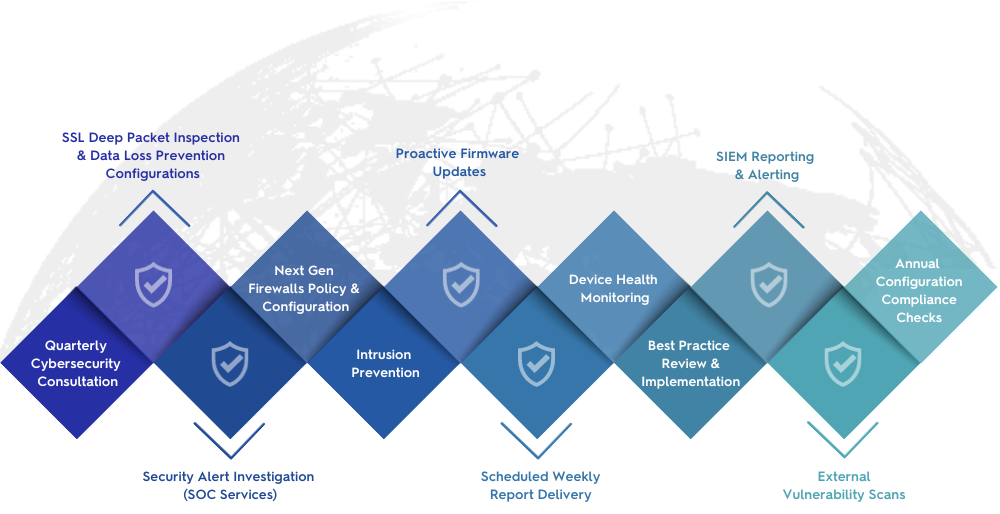






 How to Meet Changing Cyber Liability Insurance Requirements
How to Meet Changing Cyber Liability Insurance Requirements


