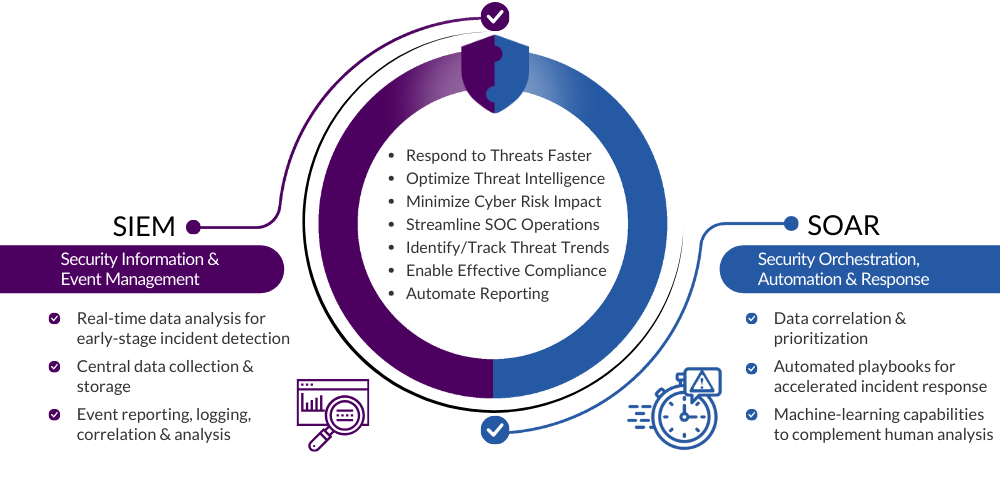
SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both essential components in cybersecurity, but they serve distinct purposes within the security infrastructure. SIEM is primarily focused on collecting, analyzing, and correlating log data from various sources across an organization’s network to identify and respond to security incidents. It acts as a central nervous system, providing real-time monitoring and historical analysis of security events, helping organizations detect and mitigate potential threats.
SOAR takes a step further by incorporating orchestration and automation into the incident response process. SOAR platforms enable security teams to streamline and automate response activities, allowing for a more efficient and coordinated approach to security incidents. These platforms integrate with various security tools, enabling automated response actions based on pre-defined playbooks. SOAR not only accelerates incident response times but also enhances consistency and reduces the manual workload for security analysts.
In essence, while SIEM focuses on monitoring and analysis, SOAR adds a layer of automation and orchestration to improve the overall effectiveness of a cybersecurity program.