
2024 has proven to be a year of significant cybersecurity challenges. High-profile attacks, such as the $1 billion ransomware incident at CDK Global, the theft of millions in tokens during the EigenLayer breach, and the Billericay School data breach, serve as stark reminders of how vulnerabilities can emerge from both human error and sophisticated cyber tactics.
While headlines captured the shock, the true story played out in boardrooms and IT departments battling ransomware, supply chain vulnerabilities, and sophisticated phishing attacks. Now that we’re turning the page to 2025, a crucial question emerges: how can we proactively build a more secure digital future?
While there are infinite steps that can be taken, we’ve narrowed down our recommendations to 25 actionable cybersecurity priorities. Built on hard-won lessons, consider this a helpful roadmap to fortify your organization’s digital infrastructure, counter future threats, and build a resilient cybersecurity posture in 2025 and beyond.
Adopt a zero-trust framework: never trust, always verify. Instead of relying on a single perimeter wall, zero trust treats every access attempt as a potential breach, meticulously scrutinizing each user, device, and action. No more giving out the “keys to the kingdom”; zero trust security restricts user access, requiring continual verification and authentication, while continuous monitoring and network segmentation build a layered defense around your most critical data.
Eliminate the challenges of building a security team from scratch with managed detection and response (MDR). Going beyond traditional SIEM alerting platforms, this comprehensive managed cybersecurity solution includes a dedicated team of security professionals who actively monitor and respond to incoming threats, neutralizing potential attacks before alarms sound.
Empower your team to be your first line of defense against cyber threats with a strategic security awareness program. Move beyond dusty lectures and yawn-inducing presentations. Engage every end user in immersive scenarios and provide hands-on anti-phishing prevention training. Equip them with the cyber-sleuthing skills necessary to identify phishing red flags, report suspicious activities, and effectively serve as your human firewall, especially as AI-powered tools enable more sophisticated phishing attempts.
Stay ahead of potential threats by regularly conducting vulnerability scans. These scans identify weaknesses in systems and applications, both externally and internally, so you can patch vulnerabilities before bad actors can exploit them. Plus, a proactive vulnerability management strategy not only helps secure your environment but also aids regulatory compliance and cyber liability insurance demands.
Implement robust data encryption measures to protect sensitive information from unauthorized access. Encryption converts sensitive information into a coded format, rendering it unreadable without the corresponding decryption key. In the event of a data breach, even if unauthorized access occurs, the encrypted data remains indecipherable and unusable.
Harness AI’s capabilities to enhance real-time threat detection and automated response. Organizations using AI report a 35% boost in threat detection rates and faster, more accurate incident handling by pairing AI insights with human intelligence. With endpoint discovery and asset management expected to expand to 50% within three years, AI helps address security staffing shortages and manage high volumes of incidents.
Leverage machine learning (ML) to build adaptive, proactive defenses by identifying evolving threat patterns and potential vulnerabilities before they materialize. Currently, 34% of security teams use ML to recognize new, unusual activities, and they plan to increase ML’s role in early anomaly detection and proactive threat intelligence. This focus on pattern analysis equips teams with scalable defense mechanisms, making ML essential for anticipating and adapting to future threats.
Segment your networks to contain and mitigate the impact of potential breaches. This practice limits lateral movement for attackers and reduces the scope of security incidents. It also enables your security team to apply tailored security measures to different segments, aligning with their unique security requirements and data/system sensitivities. This strategy is crucial for minimizing potential damage in the event of a successful data breach.
Follow industry best practices to secure cloud environments effectively. As organizations increasingly migrate to the cloud, ensuring the security of cloud-based data and applications is paramount. Adhering to established best practices, including robust access controls, encryption protocols, regular security audits, and vigilant monitoring, mitigates risks and fosters a secure cloud computing environment. Certain industries, such as local government, require specific cloud security controls to meet compliance requirements such as CJIS.
Speaking of compliance, regularly assess and ensure compliance with cybersecurity regulations and standards. Compliance assessments not only help your organization adhere to legal requirements but also enhance your overall security posture. Aligning with industry regulations demonstrates a commitment to robust cybersecurity practices, building trust and confidence among customers and stakeholders. Cyber assessment services such as Smart Comply can help you cross-walk your existing controls against specific regulatory frameworks including NIST, SEC, HIPAA, GLBA, SOC 2, and more.
Regularly review and manage user access permissions to prevent unauthorized access. User access reviews help your organization maintain the principle of least privilege, ensuring that users only have access to the resources necessary for your roles. This proactive approach reduces the risk of unauthorized access and potential security breaches.
Deploy solutions to detect and prevent potential threats from within the organization. Insider threats, whether intentional or accidental, pose a significant risk. Insider threat detection systems monitor user behavior and identify anomalies, enabling swift response to mitigate potential risks.
Elevate endpoint detection and response (EDR) capabilities with automated moving target defense (AMTD). Drawing inspiration from military strategy, where a constantly moving target is harder to attack than a stationary one, AMTD technology introduces dynamic movements across your network environment to continually alter the attack surface. These obfuscations or morphing of attack surfaces disrupt an attacker’s cyber kill chain, significantly reducing exposed attack surfaces and increasing the cost of reconnaissance and malicious exploitation. The combined force of EDR and AMTD ensures a proactive defense against evolving threats.
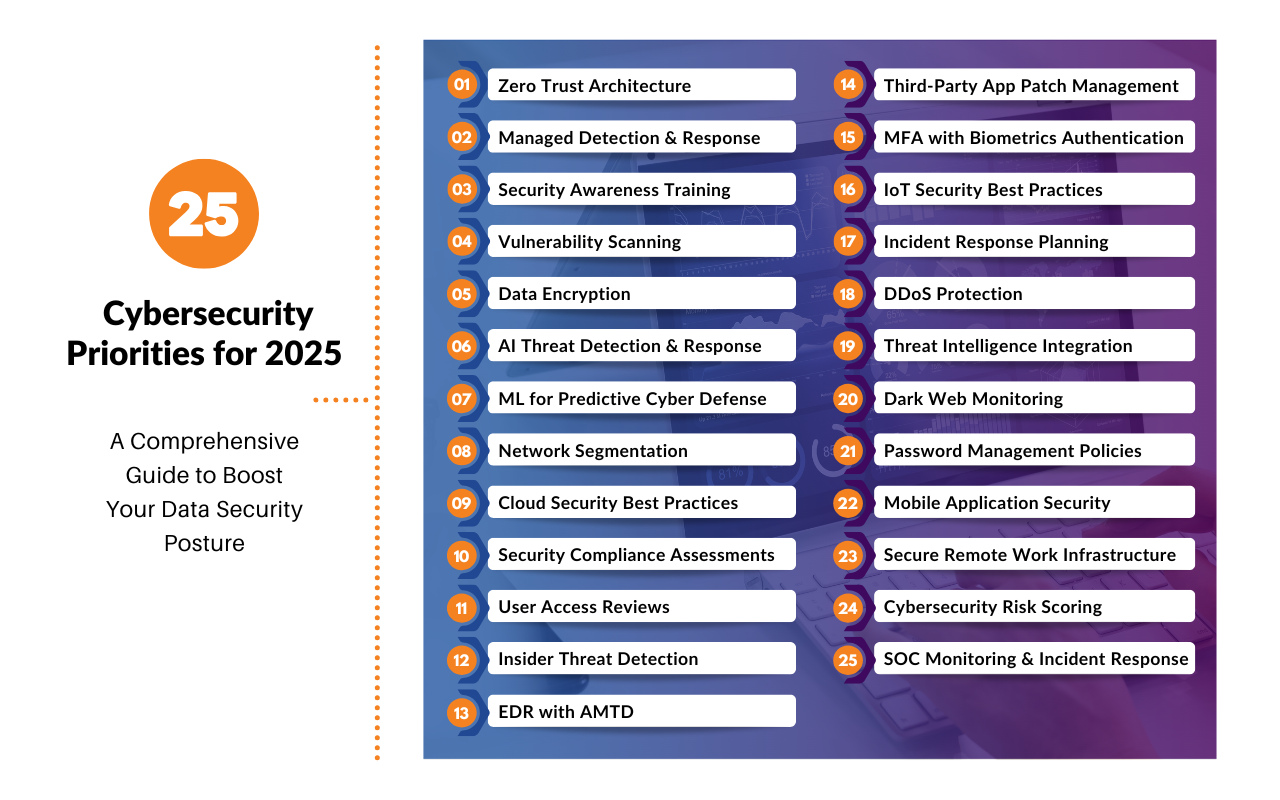
Implement rigorous patch management for third-party applications to address vulnerabilities promptly. Unpatched software is a common entry point for cyber threats. Proactive patch management ensures that all applications are up to date, reducing the risk of exploitation by malicious actors.
Evolve multi-factor authentication (MFA) by incorporating biometrics for a uniquely personal layer of security. Biometric authentication leverages inherent physical or behavioral traits, such as fingerprints, facial features, or voice patterns, adding a highly individualized and difficult-to-replicate element. This next evolution of MFA enhances resilience against unauthorized access attempts and MFA fatigue attacks, strengthening MFA by augmenting the knowledge and possession factors for a robust and sophisticated approach to authentication.
As device connectivity widens your organization’s attack surface, prioritize strong encryption, MFA, and stringent access controls. Proactively defend against IoT threats by updating firmware, conducting security audits, and enforcing device-level authentication. Embrace real-time monitoring, utilizing anomaly detection and behavioral analytics to swiftly respond to potential threats, ensuring ongoing resilience in your interconnected ecosystem.
Combine red team exercises and incident simulation drills to test and improve incident response planning. Red team exercises simulate real-world cyberattacks, allowing your organization to assess your readiness and response capabilities. By integrating incident simulation drills, your organization can refine your incident response plans, ensuring a coordinated and effective response to security incidents.
Implement robust measures to defend against Distributed Denial of Service (DDoS) attacks. DDoS attacks can disrupt online services, causing downtime and financial losses. Comprehensive DDoS protection strategies, involving techniques such as traffic filtering, rate limiting, and the use of content delivery networks (CDNs), mitigate the impact of these attacks, ensuring the continuous availability of online resources.
Leverage automated threat intelligence feeds to stay one step ahead of emerging threats. Real-time threat intelligence offers valuable insights into the latest tactics, techniques, and procedures employed by cyber adversaries. By automating the ingestion of threat intelligence, your organization can make informed decisions and proactively adjust security measures to counter evolving threats.
Look beyond the traditional walls of the Internet and utilize an MSSP for dark web monitoring, a crucial component of modern managed detection and response (MDR) solutions. Dark web monitoring identifies potential threats and compromised credentials on the dark web, allowing your organization to take preemptive action. As part of an MDR strategy, dark web monitoring enhances overall threat visibility and response capabilities.
Enforce strong password management policies to reduce the risk of unauthorized access. Weak or compromised passwords are a common vulnerability. Robust password management policies, including the use of complex passwords and regular updates, bolster the security of user accounts and prevent unauthorized access.
Implement security measures to protect mobile applications and the data they handle. As mobile usage and hybrid workforce continues to rise, securing mobile applications becomes critical. Robust mobile application security measures safeguard against threats such as data breaches, unauthorized access, and malicious app behavior.
Create a secure remote work infrastructure by instructing employees to use secure Wi-Fi connections, reducing the risk of unauthorized access. Enforce the mandatory use of encrypted VPNs, implement various remote access security measures, and adopt a company-wide secure file-sharing platform with built-in encryption and access controls. These measures collectively ensure a safe and productive remote work environment.
Develop a comprehensive risk scoring system to prioritize and address potential threats effectively. Cybersecurity risk scoring not only sheds insights into your most vulnerable security gaps, but can correlate weaknesses to direct financial costs, giving you a window into the potential cost of a breach. This systematic approach enables your organization to allocate resources efficiently, focusing on the most critical threats to your security.
Strengthen your security monitoring and incident response capabilities by utilizing an outsourced Security Operations Center (SOC) This comprehensive solution gives you access to a 24×7 dedicated SOC that delivers continuous monitoring, threat detection, and incident response services. By collaborating with a specialized external SOC, your organization gains dedicated expertise and resources to help you boost your organization’s overall cybersecurity posture – and you don’t have to incur the cost and burden associated with hiring, training and retaining in-house security resources.
Navigating the perplexing cybersecurity landscape can feel daunting, but you don’t have to face it alone. Consider Omega Systems as a trusted partner, offering award-winning expertise and dependable support. We’re not just a toolbox of technology; we provide long-term, cost-efficient solutions to not only help you combat evolving threats but also navigate compliance complexities and stakeholder expectations. Our in-house SOC, tirelessly monitors, detects, investigates, and responds to any suspicious activity, preventing incidents before they turn into costly disasters.
The 25 priorities outlined here aren’t just abstract concepts; they’re actionable steps toward a fortified cybersecurity posture in 2025 and beyond. Translating them into reality requires experienced guidance and seamless collaboration. This is where Omega Systems excels. We provide a comprehensive security ecosystem, built on deep expertise and a shared commitment to your organization’s success.