

Cyber threats are constantly evolving, posing significant risks to individuals and businesses alike. Two of the most common types of cyberattacks are phishing and smishing. While both tactics aim to deceive users and steal sensitive information, they employ different delivery methods and require unique preventive measures. Understanding the differences between these two cyber threats is crucial for protecting your data and assets. In this article, we’ll dive into the mechanics of smishing and phishing, how they operate, and steps you can take to defend against them.
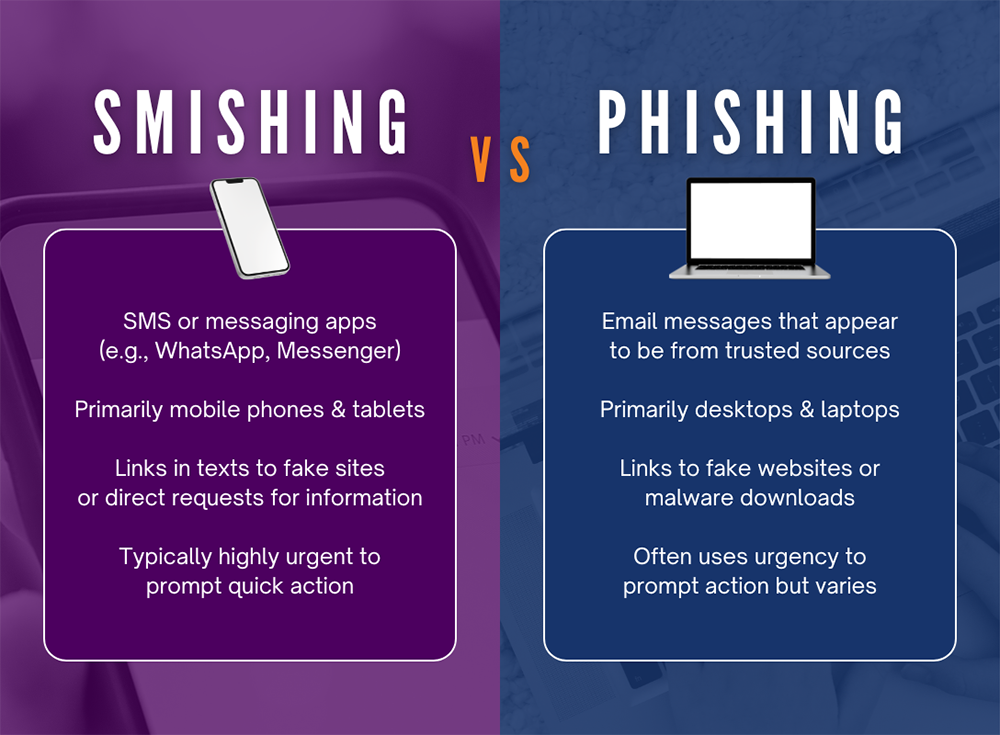
Phishing is a cyberattack in which malicious actors impersonate legitimate entities, typically through email, to trick recipients into revealing personal information or downloading malware. The goal is usually to gain access to sensitive information, such as login credentials, credit card numbers, or company data.
Smishing, short for SMS phishing, is a variation of phishing that targets victims via SMS or text messages rather than email. Smishing scams often play on urgency, directing recipients to click a link or respond with personal information under the pretense of important or time-sensitive issues.
Phishing can be challenging to detect, especially as these attacks have grown more sophisticated. Here are some best practices to help guard against phishing:
Smishing can be harder to spot, given the trust people often place in text messages. Here are strategies for defending against smishing attacks:
At Omega Systems, we understand the unique cybersecurity needs of modern businesses. Our managed IT services include advanced cybersecurity measures designed to protect your organization from threats like phishing and smishing. Here’s how we can help:
Smishing and phishing may seem similar, but they represent unique threats that require different strategies to address. By understanding the distinctions and adopting essential cybersecurity practices, individuals and businesses can significantly reduce their risk of falling victim to these scams. Contact the Omega Systems team to learn more today.